Project Overview #
Implemented a comprehensive DevOps solution for deploying the YelpCamp application (a full-stack web application for campground reviews) across multiple environments. The project established an automated pipeline covering local, containerized, and AKS environments, ensuring consistency, reliability and scalability. Infrastructure as Code with Terraform was used for provisioning resources, while Jenkins pipelines handled continuous integration and deployment processes including code quality checks and security scans.
Architecture #
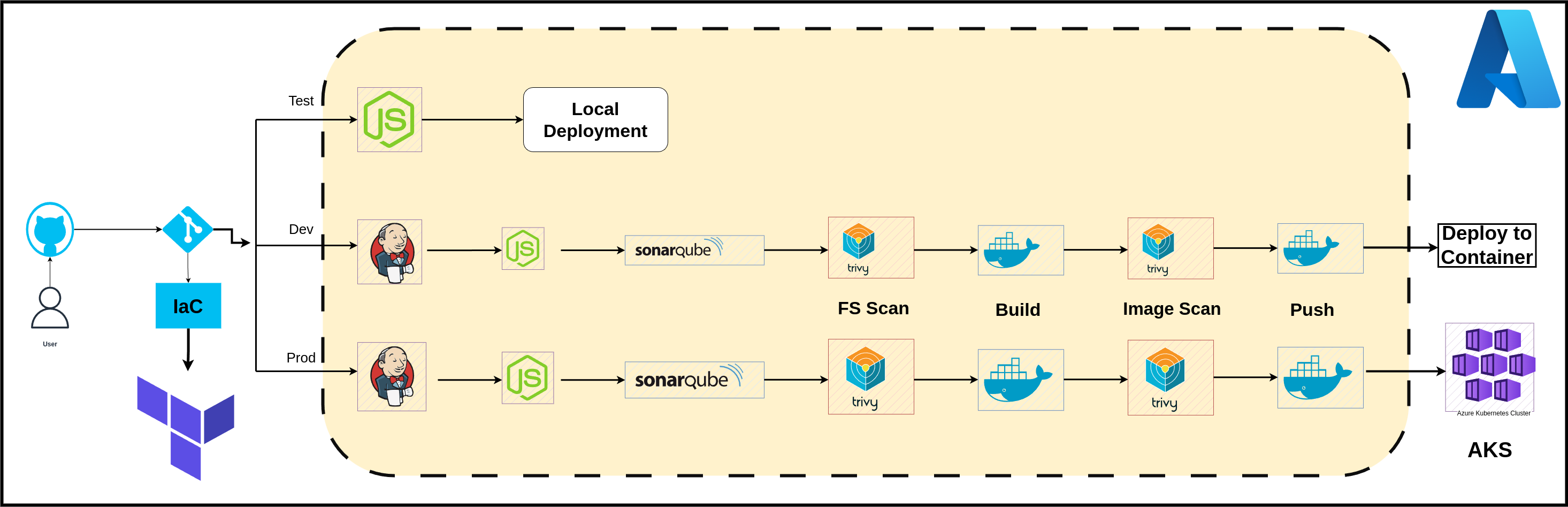
Hands-On Experience #
- Gained practical experience with infrastructure automation and modern DevOps practices
- Personally architected Terraform modules for infrastructure provisioning using workspaces
- Implemented Jenkins pipelines integrating code quality and security checks
- Configured Kubernetes deployments for production environments
- Solved real-world challenges related to secret management
- Developed environment-specific configurations for consistent deployments
- Implemented secure deployment practices across the pipeline
- Enhanced skills in designing scalable and maintainable infrastructure solutions
- Worked directly with cloud services and container orchestration platforms
Tech Stack #
- Infrastructure: Terraform, Azure (AKS, VMs, Key Vault, NSG, Blob Storage)
- CI/CD: Jenkins
- Containerization: Docker
- Orchestration: Kubernetes (AKS)
- Quality & Security: SonarQube, Trivy
- Database: MongoDB
- Application: Node.js
- Additional Services: Cloudinary (media), Mapbox (maps)
Project Links #
YelpCamp(3-tier architechture) application deployed across various environments, deployment process covering local, containerized, and Azure Kubernetes Service (AKS) using modular terraform code , CICD perfomred on jenkins.
Blog Post

