Project Overview #
Designed and implemented a comprehensive DevSecOps pipeline for a Board Game Review application, deployed on a self-managed Kubernetes cluster in Google Cloud Platform. This project integrates security at every stage of the software development lifecycle, from code commit to production deployment. By incorporating automated vulnerability scanning, compliance checks, and continuous monitoring, the solution achieves a balance between development velocity and security posture, reducing time-to-market while maintaining robust security standards.
Architecture #
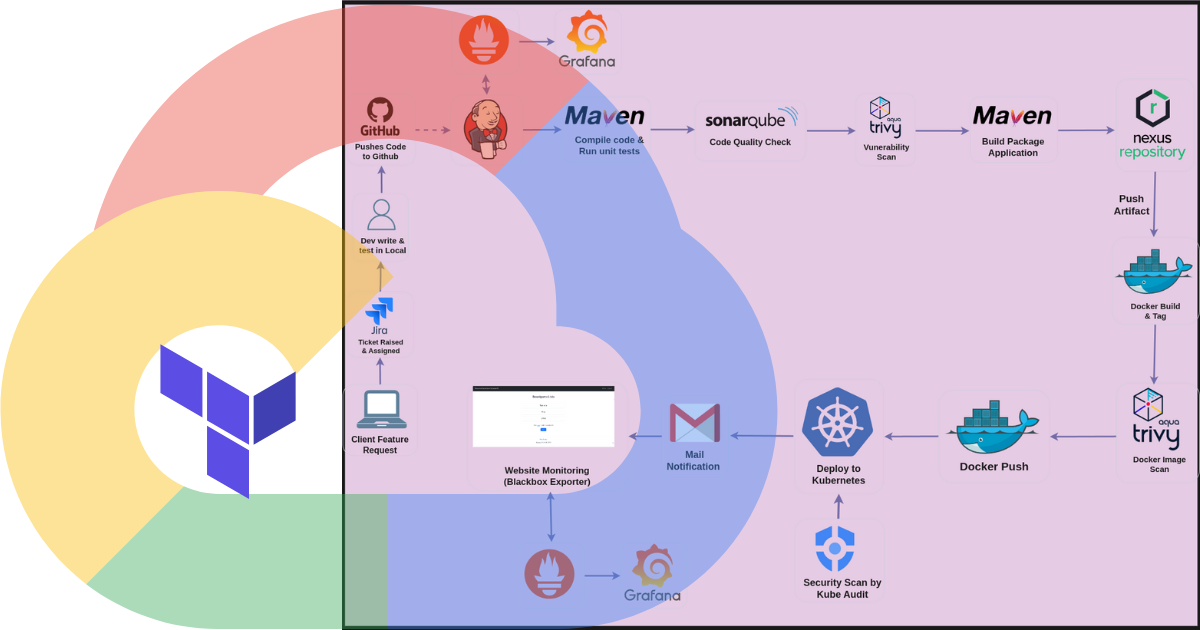
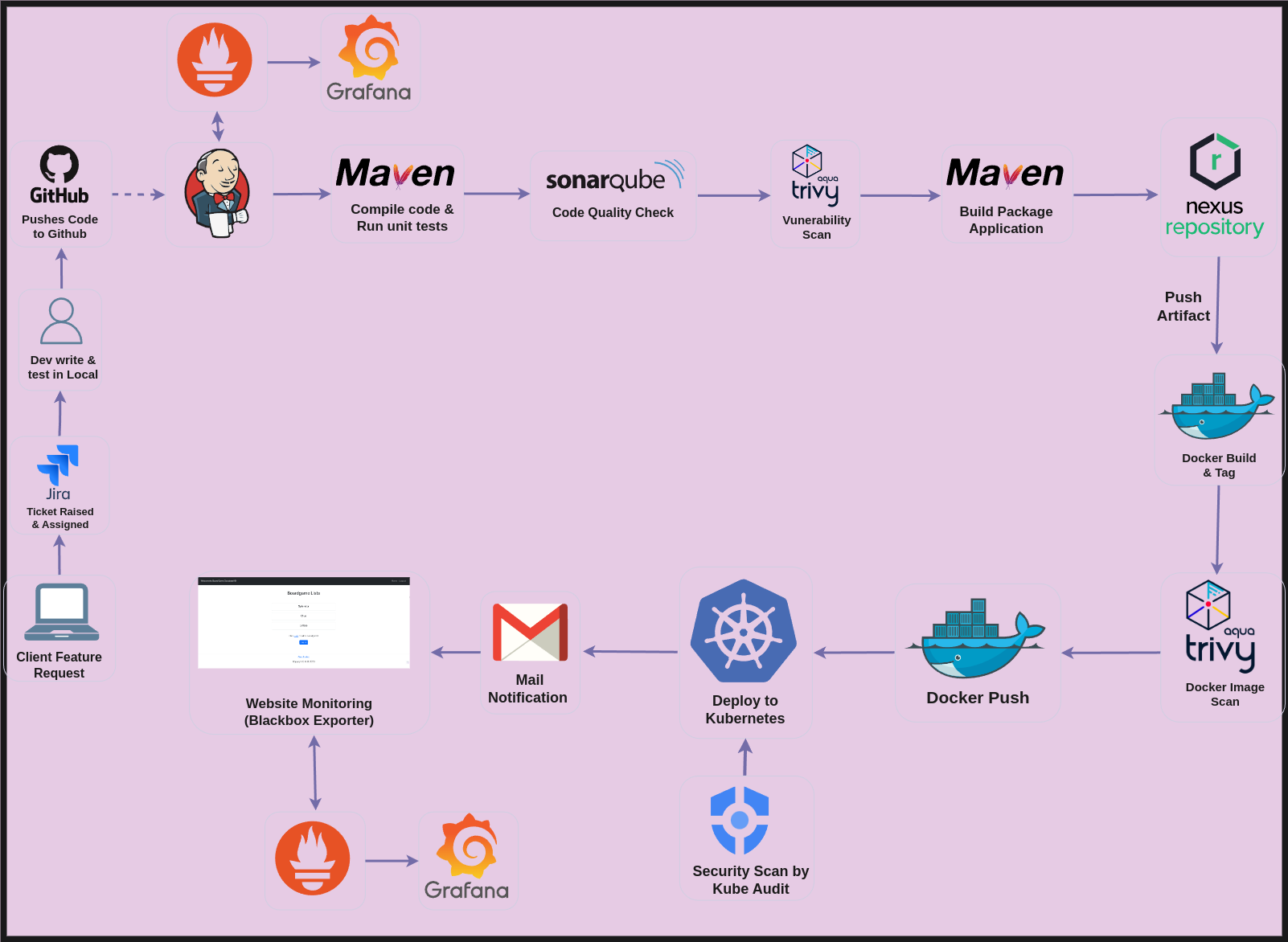
Hands-On Experience #
- Architected an end-to-end DevSecOps pipeline integrating development, security, and operations workflows
- Implemented infrastructure as code using Terraform to provision and manage GCP resources
- Set up Jenkins CI/CD pipeline
- Integrated SonarQube for static code analysis with quality gates blocking insecure code from proceeding
- Implemented Maven for build automation with dependency checks for third-party vulnerabilities
- Configured Nexus Repository for artifact storage and management with secure access controls
- Deployed Aqua Trivy for container image vulnerability scanning, preventing deployments with critical issues
- Set up Kubeaudit for Kubernetes security posture monitoring and compliance verification
- Established comprehensive monitoring using Prometheus and Grafana with custom security dashboards
- Configured email notification system for security alerts and pipeline status updates using Jenkins Email Extension plugin
Tech Stack #
- Infrastructure: Terraform, Google Cloud Platform (Compute Engine, VPC, Cloud Storage)
- CI/CD: Jenkins
- Build & Repository: Maven, Nexus Repository
- Containerization: Docker
- Orchestration: Kubernetes (self-managed cluster)
- Security Tools: SonarQube, OWASP Dependency Check, Aqua Trivy, Kubeaudit
- Monitoring & Alerting: Prometheus, Grafana, PagerDuty
Project Links #
DevSecOps Pipeline ensures secure, automated, and continuously monitored CI/CD processes on GCloud. It integrates security by design, leverages automation through Jenkins and Docker, and employs continuous monitoring with Prometheus and Grafana to maintain application and infrastructure health.
Blog Post

