Project Overview #
This project—Azure Lockdown: Securing Workloads with Azure Virtual Network Controls—focuses on implementing robust security measures around Azure workloads using network isolation, NSGs, service endpoints, and private links. The goal was to reduce the attack surface, enforce least-privilege access, and ensure workloads are only reachable through secure and intended paths. The entire solution is automated using Terraform for scalable and consistent deployments.
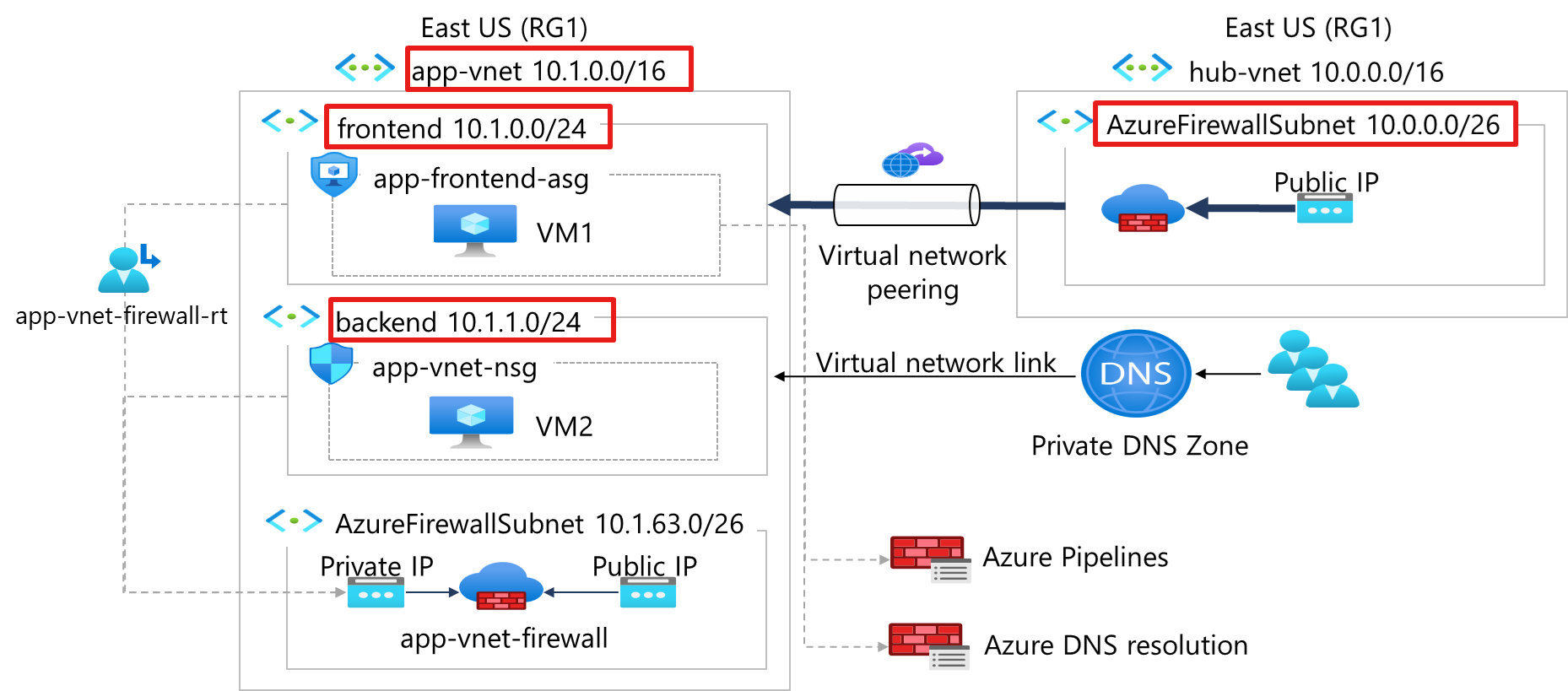
Architecture #
Hands-On Experience #
- Designed and implemented a zero-trust networking model using Azure Virtual Networks (VNets)
- Created isolated subnets for different workloads—web, application, and data tiers
- Applied Network Security Groups (NSGs) with fine-grained inbound/outbound rules to control traffic
- Enabled Service Endpoints for secure access to Azure services like Storage and SQL without exposing them publicly
- Configured Private Endpoints for sensitive resources to block all public access
- Integrated Route Tables for custom routing between tiers and to restrict internet access where not needed
- Validated the setup with end-to-end testing using virtual machines, NSG flow logs, and Azure Monitor
Tech Stack #
- Cloud Platform: Microsoft Azure
- Networking: Virtual Networks, NSGs, Route Tables, Service Endpoints, Private Endpoints
- Security: Zero Trust Architecture, Least-Privilege Access
- Monitoring: Azure Monitor, NSG Flow Logs
Project Links #
vsingh55/AzureLockdown-Securing-Workloads-with-Azure-Virtual-Network-Controls
The project focuses on network isolation, traffic control, protection against malicious traffic, routing, and DNS configuration to enhance the security posture of the network.
null
0
0

