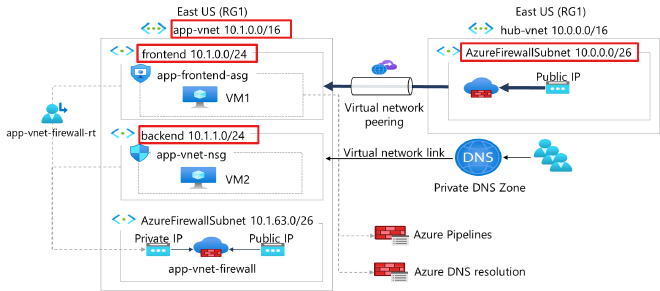
vsingh55/AzureLockdown-Securing-Workloads-with-Azure-Virtual-Network-Controls
The project focuses on network isolation, traffic control, protection against malicious traffic, routing, and DNS configuration to enhance the security posture of the network.